
The first part in our series on taming the uncertainty of ransomware risk spotlighted a playbook approach to reduce the conceptual uncertainty surrounding ransomware risk. In this sequel, we drill down to offer a risk factor-based approach to help tame the empirical uncertainty surrounding this cyber risk.
Reducing Empirical Uncertainty: Risk Factors as Risk Differentiators
In addition to playbook framing, in practice, ransomware uncertainty can be tamed by leveraging signals of distress that actually correlate to this peril. Guidewire Cyence (Cyence) has developed meaningful risk insights to help identify which companies may be at higher risk of a successful ransomware incident. Rather than relying on instinct or educated guesses, insurers and organizations can now turn to threat and exposure signals to select and quantify ransomware risk at both firm and portfolio levels, as well as deploy controls that prevent and mitigate ransomware incidents. While correlation of these risk factors and risk ratings with ransomware more directly assists with frequency estimates, risk selection, and risk prevention, it can have comparative ranking and trend implications for risk pricing and capital allocation.
Using threat and exposure signals along with real incident data, Cyence conducted correlation analyses to discover the discrimination power of risk factors and risk ratings with ransomware incidents.
The results show the discrimination power of risk factors for ransomware. Specifically, the likelihood of a company having a ransomware incident increases by the following multiples if an organization exhibits the following risk signals:

The results below indicate the predictive value of the top 3 risk factors for all industry sectors. The top four sectors with historical ransomware incidents are education and research, healthcare, public administration, and financial services.
Targeted Darkweb Chatter (45x Discrimination Power)

This risk factor comprises specific and focused discussions about the company within the hacker community. Hackers use underground forums for a variety of activities: sharing ideas, tips, and tricks; planning and executing attacks; and even boasting about the latest successful hack. Increased hacker forum activity generally signals that a company has recently been breached or is being targeted for an attack.
Leaked User Accounts (22x Discrimination Power)

Leaked user accounts can include email addresses used for registration, subscription, or account login.
User accounts and online identities shared or sold on the dark web could be used to target individuals in spear phishing campaigns aimed at obtaining sensitive information.
Ransomware is distributed by actors buying access to a company’s secure network. Leaked user accounts on the dark web enable bad actors to access machines to deploy ransomware.
High Risk Rating (22x Discrimination Power)
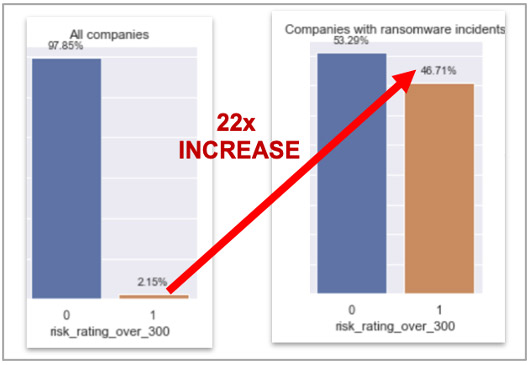
While the current Cyence risk rating measures the probability that an individual company will experience a data breach in the next 12 months, it also has predictive advantage for identifying which companies are at higher risk of a ransomware incident. If a company has a risk rating of greater than 300, the company is 22 times more likely to have a ransomware incident.
Relating Ransomware Risk Factors and Data Breach
To test the theory that predictive risk factors for ransomware can also forecast data breach, Cyence used a similar methodology to detect the relationship between ransomware risk factors and data breach incidents. The results show the discrimination power of these risk factors for predicting whether a company will have a data breach incident.
As with ransomware association analysis, we calculated how the observation of specific risk factors can be used to help identify companies with a higher risk of data breach. This calculation can be used as a metric of risk factor importance in data breach incident prediction.
Note that this initial analysis focused on the single-variable discrimination power of risk factors. Further analysis aims to determine the predictive power of multi-variable analysis. The metric was calculated both against data breach incidents and individual ransomware incidents, which enabled us to compare how similarly or differently a risk factor impacts the likelihood of different perils. Our analysis revealed a monotone trend, meaning that when a risk factor is stronger in predicting a ransomware incident, it is also likely to predict a data breach incident more effectively.
Ranking the risk factors by descending importance (where 1= most important for both perils), and then plotting the data breach risk factors against ransomware, we discovered that risk factor ranking is highly linear between the two perils. This helps validate that ransomware and data breach share certain risk signals, and therefore we can leverage the risk factor value proposition for identification and selection of both types of incidents.
As with ransomware, we back-tested against data breach incidents in 2017 to compare the importance of risk factors between back-testing and previous analysis using all incidents. Again, we discovered a strong linear relationship, thus showing consistency between back-testing and holistic analysis for correlation between certain risk factors and data breach incidents.
Closing Remarks
Part 1 in this series advanced a playbook approach to reducing conceptual uncertainty of ransomware risk, and this part reveals the value of risk factors in reducing empirical uncertainty. Stay tuned to learn more in the next and final part of this series, where we delve into the cyber insurance implications of these approaches in reducing ransomware risk.